Lync Server 2010 RC currently has no Resource Kit. Until it does, follow these instructions to grant Snooper.exe the ability to automatically analyze your Lync Logger traces. Keep in mind, this blog article will not be needed anymore once the Lync Resource Kit Tools are released.
For those of you working in a lab environment, you may need to do some more thorough troubleshooting besides looking at Event Logs. These tools that provide the ability to do further troubleshooting are located in the Resource Kit Tools. As stated above, Lync 2010 RC does not have Resource Kit Tools, yet. I’m sure most of you would then think of doing the following: to install the OCS 2007 R2 Resource Kit. But, there’s a problem. If you go to install the OCS 2007 R2 Resource Kit, you get the following error:

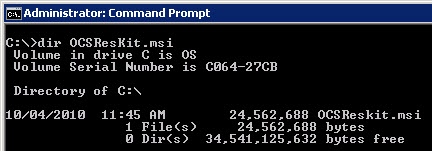
Thankfully, there is a way to get Snooper installed so that we may do some deeper analysis of Lync Server 2010 RC. The first thing we will need to do, is take the OCS 2007 R2 Resource Kit Tools, and extract the tools using msiexec. To do this, I will put the OCSResKit.msi in the C:\ volume at the root level.
We now want to build our msiexec command to extract this MSI file. The command utilized will structured as such:
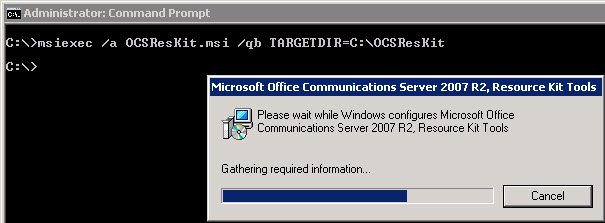
Because our cmd.exe is in the same location as the MSI file we will be extracting and we want our folder to also be located on C:\, we will use the following command:
After running the command, we will see the MSI Extraction processes which looks as if the OCS Resource Kit is installing.
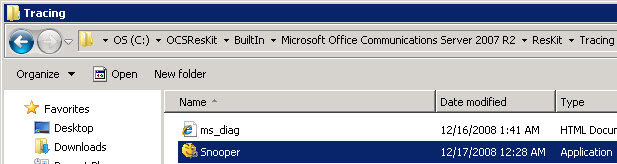
Let’s navigate to the location of our Snooper.exe. This is located in “C:\OCSResKit\BuiltIn\Microsoft Office Communications Server 2007 R2\ResKit\Tracing”
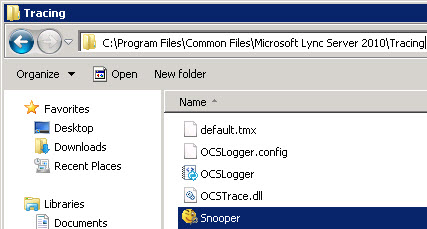
Copy the Snooper.exe executable and navigate to and paste the file in the following directory “C:\Program Files\Common Files\Microsoft Lync Server 2010\Tracing”
Now when you are doing tracing with The Lync Server 2010 Logging Tool and click Analyze, it will have the ability to automatically launch Snooper.exe just like with OCS after you had installed the OCS 2007 R2 Resource Kit in OCS 2007 R2.


Yay! This helped me install LyncDebugTools (for Lync Server 2013) on Windows 8.1 (not pro). Snooper runs like a champ!
That was very helpful
Thank you very much. That helped a lot!
I just installed the OCS R2 Reskit – no real issue doing so.
You can simply copy snooper.exe or tracing folder from any resource kit installed machine. it will work.
I would hope that'd be pretty obvious to anybody that already uses snooper.