Exchange 2010 introduced a new feature called Client Throttling. The goal of this functionality is to ensure that no one user can tax your Exchange Server. I’m sure many of us have had to troubleshoot Exchange performance issues and one of the tools that we utilize is the Exchange Server User Monitor (Exmon) tool. Often, you will find a couple users who are using utilizing the system quite a bit more than other users. We become worried and suspicious that something may be going on with this user.
With the new Client Throttling functionality, we can feel more confident of the following:
- Users aren’t intentionally taxing our Exchange Server
- Users aren’t unintentionally taxing our Exchange Server
- Users are proportionality utilizing the resources on our Exchange Server
Policies
By default, Exchange 2010 utilizes a Default Policy to manage all of the users on your Exchange 2010 Server. Should you decide that different users need to have a different throttling behavior, you can create different policies for these different user groups. Or should you decide that you want all users to have have the same throttling behavior but different parameters than what the Default Policy contains, you can modify the Default Policy to fit the needs of your organization.
The four PowerShell cmdlets that assist you in defining your policies include:
- New-ThrottlingPolicy
- Remove-ThrottlingPolicy
- Get-ThrottlingPolicy
- Set-ThrottlingPolicy
Exchange Servers Throttling Applies To
The parameters that are configured in a policy apply to the following Exchange functionality:
- Activesync
- Web Services
- IMAP
- POP
- Outlook Web App (OWA)
- PowerShell
- RPC Client Access Server
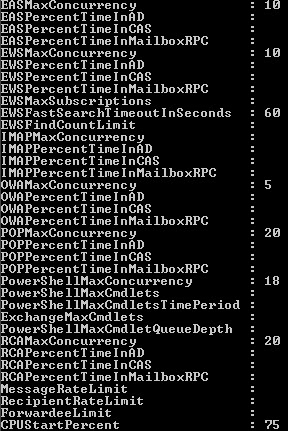
Throttling Parameters
The parameters that you will configure are:
- MaxConcurrency
- PercentTimeInCAS
- PercentTimeInAD
- PercentTimeInMailboxRPC
By default, out of these 4 parameters, MaxConcurrency is the only parameter that has a value specified. It is also the parameter you will most likely configure should you have a need to modify your throttling behavior.
Each Parameter will be prefixed by each type of Exchange Service. For example, Activesync will be EAS. Because of this, the parameter for Max Concurrency for Activesync would be EASMaxConcurrency. The acronyms for each service are:
- Exchange Activesync = EAS
- Exchange Web Services = EWS
- IMAP = IMAP
- POP = POP
- Outlook Web Access = OWA
- RPC Client Access = RCA
- PowerShell = PowerShell
The parameters for PowerShell are a bit different and include the following:
- PowerShellMaxConcurrency
- PowerShellMaxCmdlets
- PowerShellMaxCmdletsTimePeriod
- PowerShellMaxCmdletQueueDepth
Let’s take a look at configuring Activesync Throttling. We can do this by running:
Get-ThrottlingPolicy | FL IsDefault,EAS*
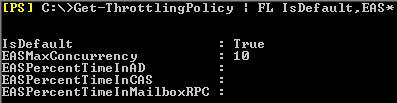
As you can see, since we haven’t created a policy, this will show us our Default Policy as you can see by the parameter IsDefault being set to True. For all Exchange services that can utilize throttling, you will see that only MaxConcurrency is configured.
CPUStart
It is important to note the CPUStartPercent parameter. It is only when Exchange reaches this CPU utilization that the policy will be enforced. If an Exchange Server is adequately sized, your user’s should very rarely ever get throttled. But throttling is good to have in the situation where your Exchange Server does encounter high CPU utilization in the circumstances noted at the beginning of this article, intentional high utilization and unintentional high utilization which the throttling policy will ensure that users are utilizing your Exchange resources proportionality.
MaxConcurrency
Maximum amount of connections that a user can have open on an Exchange Server at any given time. So by this being set to 10, once an Exchange Server utilizes 75% usage, the Exchange Server will begin throttling new connections. Keep in mind that this will only throttle “new” connections. So if a user has let’s say 15 connections open, 5 of those connections should not be disconnected. Again, you can modify the Default Policy to contain a different amount.
Example: Modify EAS MaxConcurrency
Let’s say we wanted to modify EAS to throttle and allow 12 connections. Our organization has a lot of EAS activity and we determined we want to bump up this value just a little bit. We would run the following cmdlet:
Set-ThrottlingPolicy -Identity IdentityHere -EASMaxConcurrency 12
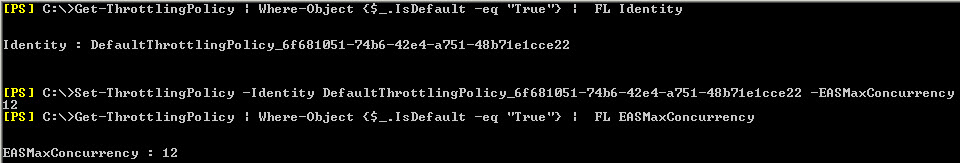
In order to obtain the name of your Default Throttling Policy, run the following command:
Get-ThrottlingPolicy | Where-Object ($_.IsDefault -eq “True”) | FL Identity
In our case, the Identity of our Default Throttling Policy is DefaultThrottlingPolicy_4f681051-74b6-42e4-a751-48b71e1cce22. Easy enough to remember eh?
This would change the above command to:
Set-ThrottlingPolicy -Identity DefaultThrottlingPolicy_4f681051-74b6-42e4-a751-48b71e1cce22 -EASMaxConcurrency 12
Remaining Parameters
As stated above, it is important to note that most of the time, you will only configure the MaxConcurrency parameter. Should you find the need to further tweak your policies, you can visit the following Technet Articles to learn more about those parameters: here and here. The articles will also show you how to create a new policy as well as assign the new policy to a specific user or a group of users.


Yes i agree that only 5 of the connections should be disconnected, however how many connections can one device open ?
I am not sure but it seems to me based on your description of MaxConcurrency, the following line should correctly read ..
So if a user has let’s say 15 connections open, 5 of those connections should BE disconnected.
Thanks for the post. A few comments:
1. CPUStart is *only* used by EWS. Once the average CPU utilization of EWS exceeds this percentage value, inbound requests will be delayed to keep EWS process CPU utilization down. This was added so that EWS would not create poor user experience for OWA users being serviced from the same box.
2. MaxConcurrency has nothing to do with CPUStart. If the current caller tries to exceed their concurrency limit, then the new requests will be killed – this is a hard limit. So with a MaxConcurrency limit of 10 you could never have a case where the caller has 15 connections.
David Sterling [MSFT]
So if we want to ensure one person doesnt use a million connections, regardless of server load, we should set cpustart to zero?
If you want to limit their connections regardless of how much CPU utilization your Exchange Server has, then yes. If you want to limit only certain users, then you can create a new policy and apply this policy only to those specific users.
cool post. Only issue with throttling isnt you wont be alerted to users doing the *dodgy* things on your system. (althought a crippled exchange server isn't really the best way of finding out about your dodgy users)