Now looking at my title, many of you may be thinking, ok so what… we have an Enterprise Issuing CA. Now here’s where a lot of people get confused with Enterprise CA vs Windows Enterprise. An Enterprise CA means that your server is an issuing CA and stores/retrieves information directly from Active Directory while a Standard CA does not. Another difference is that an Enterprise CA issues certificates based on templates while a Standard CA issues certificates based on Enhanced Key Usage (EKU). EKU is essentially a certificate that defines if a certificate can be used for Server Authentication, Client Authentication, All, Etc… An Enterprise CA will issue certificate with templates such as Web Server, Encrypting File System, Domain Controller, Etc. Each of these templates will be based on a number of factors such as what EKUs will be assigned to that template.
Now everything I have wrote above explains the difference between a Standard CA and an Enterprise CA. What about which version of Windows we use? Well, there is a difference between Windows 2003 Standard and Enterprise when it comes to your Certificate Authority. There is something called Certificate Version Templates which are known as Version 1 and Version 2 Templates. Don’t get this confused with the actual version of a certificate X.509 Version 3 is what has been used in Windows for years. A Windows 2003 Standard Edition Server that hosts your Certificate Authority that will be issuing certificates will be able to issue Version 1 Certificate Templates only. So if you ever need to create a custom template based off of an already existing template, you will not be able to. This is because when you create a custom template, it becomes a Version 2 Certificate Template.
Now Office Communications Server documentation recommends that you have an Enterprise CA. This means that the certificate information will be stored in Active Directory and when you deploy your Standard Pool Servers or Enterprise Front End Servers, you can just search for an Enterprise CA and automatically request and approve a certificate due to the machines being domain members. OCS Front End Servers or OCS Edge Servers do not require you to use Version 2 Certificate Templates. So from a perspective of Standard Pool Servers, Front End Servers, and your Internal NIC for your Edge Server, you can use Version 1 Certificate Templates. But with CWA, this is not the case.
Now this is where Communicator Web Access (CWA) is different. If you look at the planning guide for CWA, there is a section on certificates. You can view this planning information here. If you look through the document, you will see the table that describes the certificate requirements.
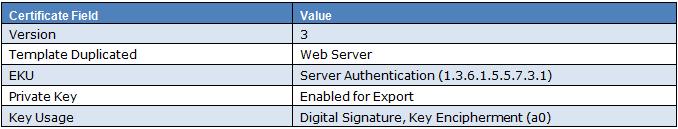
As you can see, the certificate requirements state that the Web Server template needs to be duplicated. This is both for the Mutual Transport Layer Security (MTLS) Certificate as well as the Secure Sockets Layer (SSL) Certificate. So if you are going to be deploying OCS and CWA and are planning to deploy a Certificate Authority, I would suggest that you deploy your Certificate Authority on at least a Server 2003 Enterprise Edition Operating System. Server 2008 Enterprise Edition introduces Version 3 Certificates Templates, Online Responder, Network Device AutoEntrollment Service, and Native Support for Qualified Certificates. So if you are going to be deploying a CA, it may be worth your time to deploy Server 2008 to be more “future proof.” To enable the new features of a Server 2008 CA, you will need to update your schema.
Note: I explained this earlier but I will go into it a little more. Some of you may be thinking you need a Server 2008 CA then since the table states you need a Version 3 certificate and Server 2008 CA can do Version 3 Certificate Templates. Version 3 (X.509 Version 3) certificates are not the same as Version 3 Certificate Templates. Version 3 certificates have been around since 1996 and enable functionaly such as Authority Key Identifier, Subject Alternative Names, Enhanced Key Usage, Etc… All these pieces of functionality have been in all Editions of Windows for quite some time. So Version 3 Certificates are not the same thing as Version 3 Templates.
If you did deploy Windows 2003 Standard Edition on the server which contains your Certificate Authority, you can thankfully upgrade to Windows 2003 Enterprise Edition or even Windows 2008 Enterprise Edition. If you deployed a Standalone CA and want to upgrade it to an Enterprise CA, you can follow the instructions here.
Update 1: According to Tom Pacyk, you can use the OCS Admin Tools to request a certificate that’ll provide the correct type of certificate needed for CWA. Read his comments below for further instructions.


This worked great. But I think you could get the same results by requesting the cert via the OCS MMC on another server. Set a SAN if you're using something other than the FQDN for the CWA sitename and export/import the cert onto the CWA server.
So I have a theory after looking at some stuff. The OCS documentation states that OCS requires the Web Server template to be available. Now the default template is named “Web Server.” But if you look at the detail of the certificate and look at the Certificate Template Name, it states “WebServer.” So because the names are different but it requires the Web Server, I think your assumption about OCS using its’ own temporary template is correct. I think that OCS basically uses the Web Server template, and somehow works with the CA to allow it to make a certificate based off of a temporary version 2 template so to speak and then removes it after the certificate is made. I’ll have to eventually try making a version 2 template called “WebServer” and seeing what happens out of curiousity.
No problem.
I can’t remember exactly, but I want to say the OCS cert wizard uses its own template to request the cert, hence the ability to export the private key and have SANs on it as well. It could very well be some advanced options it spits at the CA instead of a different template, but either way – you get the exact cert type you need by using that method.
And as an aside, there’s a little trick you can do with the regular Web Server template the does allow you to export the private key without duplicating the template.
Fill out the cert info as normal, pick the web server template. The “Mark private key as exportable” checkbox is grayed out. Press Submit. Instead of clicking the link to install the cert you generated, hit the back button on the browser. “Mark private key as exportable” is no longer grayed out! Check the box, press Submit again and voila – you get a cert you can export with the private key.
Thanks for the information Tom. What seems odd is that the WebServer Template does not allow you to export a private key. If you look at the Version 1 Template, it doesn’t allow the private key to be exported. If you go onto the certsrv website, the option to export as a private key is greyed out.
But if I go onto my Front End Server, it used the template for Web Server which can see by the properties of the certificate, yet the certificate has the ability to export the certificate with its private key.
So it seems like there is some mechanism in the OCS admin console that allows the certificate request to allow the certificate to be exported with its’ private key even if the template it’s using doesn’t allow that option.
In an effort to clear this up…
We’re talking operating system Enterprise vs. Standard edition – not Enterprise CA vs. Standalone CA.
CWA 2007 does not require a Server 2003 Enterprise Edition (Enterprise or Standalone) CA.
The ability to duplicate and modify a certificate template does require a Server 2003 Enterprise Edition, but you don’t necessarily have to do that for OCS. The easy way around this is to just use the OCS Certificate Wizard from the admin console. It provides the correct template (SAN entries supported) and doesn’t require.
Here are 3 alternatives to avoid having to purchase a Server 2003 Enterprise CAL.
– Install the OCS admin console on your CWA box and issue a certificate using the OCS certificate wizard.
– Issue the certificate using the OCS console on a different box, export it with a private key, import into the CWA box
– Issue some advanced certificate options via the certsrv website which will issue the SAN field.
– Use the certreq.exe tool to request a certificate with a SAN.
The latter two options are discussed in more detail here: http://support.microsoft.com/kb/931351/en-us
How do you use the OCS admin console on your CWA box and issue a certificate using the OCS certificate wizard?
I've been using the OCS Certificate Wizard on the FE ever since Tom made this post to create my CWA certificates. I've also used LCSCMD to do this. Both work fine.
I believe you and I would like to do the same thing… I do not know where to launch the OCS Certificate Wizard from the OCS Admin Console. I can do it through the Deployment Wizard but I can't seem to find it in the Console.
OCS 2007 R1 or R2?
I installed the Administrative Tools on the CWA server but could not find it. I used the Certificate Wizard on the Front End server. Thanks for your help.
I tried Tom's second option and it didn't work because I neglected to put in a SAN for the site's URL that we use internally. We had previously been working with one cert in IIS and a separate one for CWA, no SAN in either one. How this arrangement ever worked or why we used two certs originally escapes me. Tom, do you remember?
I called Microsoft and here's how they recommended I get a cert with a SAN from an internal 2003 Standard Edition CA: (To be clear, he didn't exactly 'recommend' this, I think the support engineer said something like "this might work" before I ran it.)
Run this in the command line on the CA:
certutil -setreg policyEditFlags +EDITF_AttributesubjectAltname2
Then I requested my cert from certsrv website, advanced request, server FQDN in name field, server auth cert type, marked key as exportable and store in local computer store, then in the attributes field I entered:
SAN:DNS=sitename.domain.local&DNS=server.domain.local
I added a friendly name, submitted, issued, then installed the cert via certsrv site.
Tom,
When you say SAN entries are supported, how can multiple SANS be entered? BTW, option 1 seemed to work great although it seems to completely cut out the Cert Authority server and just provides trust between the OCS FE and CWA server. Is that okay?